Take Control, Let's Talk Cyber Defense!
Beyond the Dashboard: Why Your SOC Needs a Human-Centered Command Center
Companies often sacrifice efficiency of their specialist teams for a vision of a "source of truth" combining all aspects of IT operations. From deployment of a new virtual server, incident management, change management, to SOC operations. The problem is that they under-resource this centralized service so integration of new services as well as usability deteriorates with massive impact on everyone, but cyber security teams seem to be often impacted most.
3/29/20256 min read
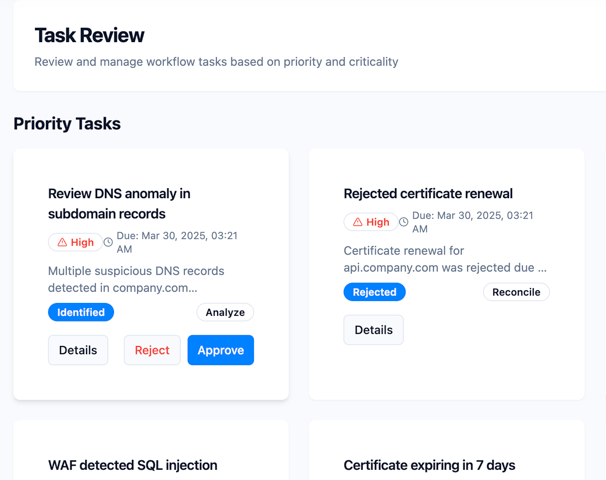
When talking with a SOC team recently - just after the Next.js (CVE-2025-29227) bug was published. The lead analyst - let's call her Maya - explained to me how complex it was to analyze the exposure. She moved from screen to screen in the same manner that a pilot does during turbulent flight conditions. Six different dashboards. Three separate logins. She emitted a deep sigh when she launched their asset management system to record her findings.
Maya made a low murmur of frustration while she clicked the submit button then watched the wheel of death spin. "Each entry takes about four minutes to load. I need to document another fifty items after finishing this one."
During the delay she showed me the process which included finding vulnerabilities then moving to the asset system followed by page loading delays before manual data entry and more waiting and repetition. Interface friction converted a one-hour task into a six-hour process.
She told me that this was normal. The team learned to accept the situation.
Enterprise security hides an unattractive truth because organizations spend millions on detection tools yet force their analysts to use interfaces that would make software developers from 20 years ago feel uncomfortable. At Axon Shield we observe this pattern multiple times: Sophisticated threat hunting capabilities accompany workflow systems which negatively impact human performance.
The True Cost of Poor SOC Tooling
Our post-incident assessments with clients show that detection failures are hardly ever caused by missing technical capabilities. Instead, they occur because:
Analytical staff members expend their mental capacity on battling their system interfaces instead of performing threat assessments.
The essential information disappears when analysts move between separate tools which do not integrate properly.
Decision fatigue develops when employees need to perform continuous context switching that proves unnecessary.
Talented team members leave, taking institutional knowledge with them
A CISO from last quarter expressed his straightforward opinion by stating that a six-figure detection tool expenditure during the previous year failed to produce better outcomes because analysts became overwhelmed by the supposed assistance tools.
The AI Revolution in Security Operations
The security environment transforms at an unprecedented pace. AI-assisted development are going to revolutionize security tooling creation by allowing organizations to design purposeful and user-friendly interfaces in short periods of days instead of requiring extensive years of development and unlimited budget allocations.
At Axon Shield, we have been developing an engagement process that speeds up and automates IT support for cyber security standard operating procedures (SOC). Organizations that accepted inferior workflows for too long now possess the ability to redesign their operational structures.
The main achievement goes beyond speed because it enables adaptability. Your tools will operate in near real-time to adapt to changing response playbooks which inevitably occur. Your defensive capabilities maintain the same pace as the threats you encounter because of this agility.
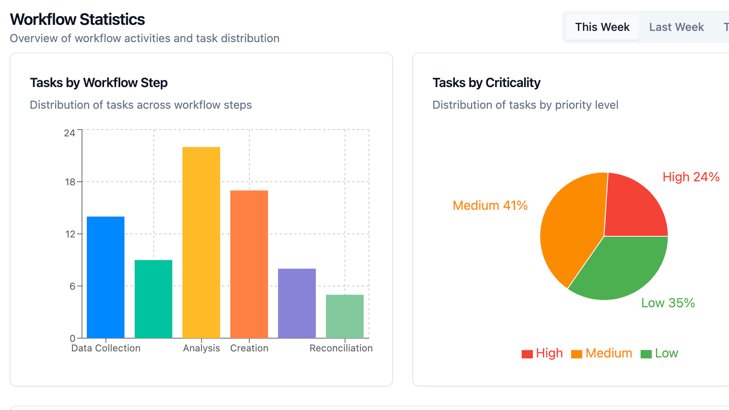
The Axon Command Center
Our technology is based on a "Human Command Center". It represents a new workflow management approach for security operation centers which focuses on how security professionals operate.
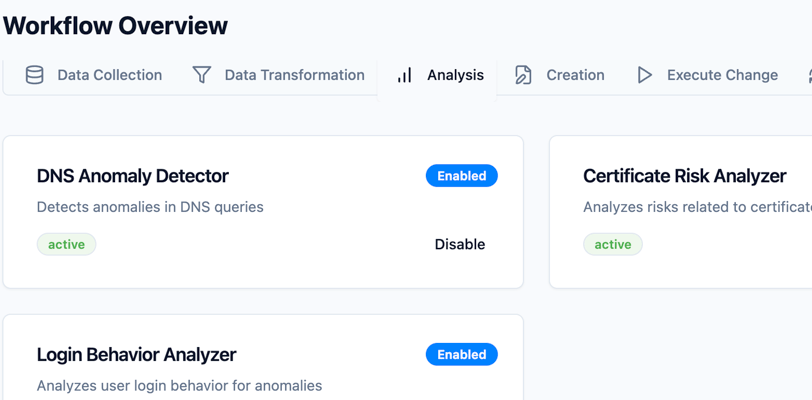
Our team has evaluated SOC (security operations centers) of our clients over several years. Based on our experience and findings, we've created a workflow framework that with pluggable design for integration of new tools, change management procedures, and decision processes. We use AI technology to quickly deliver not only API-based integrations with customer existing tools but also tailored user interfaces to fit into your environment. Here's what we've learned matters most.
Unified Cognitive Workflow
All successful SOCs we have worked with combine their defensive processes into one coherent workflow structure that follows the logical thought patterns of analysts. The workflow begins with data collection integration and transformation followed by smooth transition into analysis and response planning stages before finishing with action execution and exception handling.
Human-Calibrated Role Design
The usual role-based access controls fail to match the real-time collaboration patterns that people exhibit when handling security incidents. Security teams must have defined roles and skillsets, which is the starting point. The magic happens when "doing things" supported with the right technology, allows team members to learn and gain experience and automatically be promoted to resolve issues independently.
Our field assessments demonstrate that operators maintain focus and effectiveness when their work is chunked into small, manageable batches of tasks. Work tasks consisting of six items not only motivates us to complete the work quickly but makes us feel good about delivering results. The difference between detecting an intrusion and missing it is often due to analysts facing cognitive overload.
Not the least, we often become paralized by the sheer size of a "big problem". What we need instead is to start making steps - one at a time.
Performance Intelligence That Drives Improvement
The number of alerts processed offers minimal insight into team performance levels. Our clients benefit from the implementation of more useful performance metrics which include time-to-decision, accuracy and other metrics. These are measured across different action types and patterns in rejected actions that signal training requirements along with team performance comparison and time horizon-based trend analysis.
The entire team achieves better performance transparency through visible metrics that avoid damaging psychological safety in a way we learned during hundreds of post-incident review sessions.
Implementation Lessons
Ability to build task-focused user interfaces and human-centric workflows solves the biggest problem of any cyber-security directory: scarcity of resources.
Focus on operations, rather than learning operating SaaS tools allows you to build skills of your team around your priorities. At the end of the day, what you need to deliver is a report to your board showing the performance in improving maturity of your operations and security delivered for your company.
Outcome-Aligned Data Architecture
Your data architecture should mirror human workflow instead of technical distinctions. The data architecture should include separate storage of data collection and analysis-ready data and purpose-built views tailored for human analysis and action tracking that logs decision context along with results.
Adaptive Workflow Configuration
Your management system needs to adapt to security needs that change frequently without demanding additional development sprints. Your system should include adjustable approval thresholds and different time limits based on criticality levels as well as modular features which become operational when needed.
Our assessments show that ability to react new threats is paramount. The Next.js vulnerability mentioned above required custom tools being built, and used to test across the whole of the internet perimeter. It was only possible due to SME expertise and integrated database of DNS data.
Human-Factor Visual Design
The appearance of an interface determines operational success rather than following aesthetic standards. Our company promotes a unified navigation system that uses clear information structures and reduced visual distractions and adaptable designs which function across multiple platforms and equipment.
Removing clutter and irrelevant information from operational screens shortens training times, improves focus and provides for efficient analysis of relevant information and accurate decision making.
The Bottom Line: Human Effectiveness Equals Security Effectiveness
Our decade-long experience assisting organizations enhance their security operations has proven that human capabilities determine your security program's effectiveness. Advanced detection rules together with response playbooks become useless when employees must struggle against their security tools instead of using them effectively.
This isn't just theory. The evidence is clear and documented. Organizations that invest in human-centered security workflows experience:
Security Operations Centers (SOCs) which use AI-driven human-centered workflows can resolve incidents 30% faster which leads to accelerated decision-making and response speed. The research published in arXiv during 2024 shows that "Evaluating the Impact of Generative AI in SOCs" resulted in these findings.
The implementation of workflow clustering and interface design reduces analyst information overload by as much as 90% which eases cognitive load while decreasing the risk of burnout. The study published in arXiv during 2022 titled "Clustering Workflows for SOC Analysts" demonstrated these findings.
The implementation of process mining combined with workflow optimization leads to an 85% increase in service delivery speed when conducting essential security briefings. The research published in arXiv during 2024 titled "Process Mining in Digital Security Services" presents these findings.
Like with many aspects of our lives - new AI-based technologies should make you go back to first principles. Forget assumptions based on outdated financial and resource costs and re-build your cyber defense strategy to reflect agility available with new IT tools.