Take Control, Let's Talk Cyber Defense!
The Science of Digital Fingerprinting for WAF Integration
Advanced Persistent Threats (APTs) pose significant cybersecurity challenges, necessitating a shift from traditional attribution techniques to behavioral biometrics. This approach focuses on human behavior patterns to create digital fingerprints for Web Application Firewalls (WAFs), enhancing threat detection. Key components include temporal patterns, technical signatures, and operational methodologies. Leveraging AI and Machine Learning furthers this analysis, while real-time integration with security systems strengthens defense mechanisms. Despite challenges, such as data quality and ethical concerns, behavioral biometrics represent the future of cybersecurity, improving attribution capabilities and enabling proactive defenses against evolving threats.
5/23/20257 min read
Introduction: Elevating Web Application Security with Behavioral Biometrics
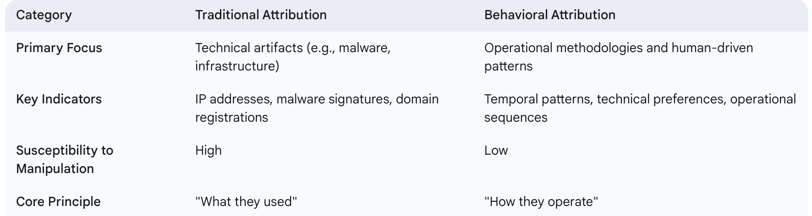
Advanced Persistent Threats (APTs) present a major cybersecurity problem through skilled state-sponsored cyber actors who execute prolonged network penetration strategies to steal data or disrupt systems. Current traditional attribution techniques using simple IP addresses and malware signatures no longer function effectively as tools for identification. Organizations have moved away from traditional attribution practices because behavioral biometrics now focuses on operational methods instead of tool identification to establish more stable digital signatures.
This transformation requires human behavioral patterns because they prove hard to replicate artificially. Web Application Firewalls (WAFs) now include behavioral analysis as a standard feature which detects human-driven patterns allowing them to serve as essential elements in contemporary APT attribution systems.
APT Behavioral Analytics: Actionable Insights for WAFs
Behavioral biometrics analyzes threat actor operational patterns to generate distinctive digital fingerprints which WAF systems can use for APT detection and mitigation.
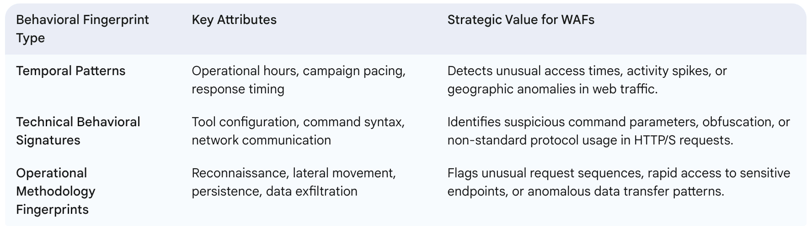
Temporal Behavioral Patterns: Threat actors follow predictable operational patterns that emerge from their geographical locations and work routines. The analysis of behavior in WAF systems allows identification of abnormal login patterns and high activity during off-peak business hours or regular access activities that match specific international time zones thus indicating APT reconnaissance or active operations.
Technical Behavioral Signatures: Attackers generate unique technical signatures through their tool deployment methods by showing particular command line syntaxes and argument arrangements along with scripting approaches. A WAF conducts HTTP request analysis to detect sophisticated attacks through the identification of unusual command parameters and obfuscation methods and non-standard protocol behavior that differs from typical application usage.
Operational Methodology Fingerprints: The sequential and strategic execution of attack phases creates distinct behavioral signatures that include reconnaissance approaches alongside lateral movement techniques and data exfiltration patterns. WAF systems detect suspicious web request patterns as well as rapid exploration of sensitive areas and unusual data transfer amounts and distributions which signal the progression of an APT attack.
Advanced Behavioral Analysis Techniques: Leveraging AI and Machine Learning
The processing of extensive data sets along with the detection of faint behavioral patterns depends heavily on AI and Machine Learning (ML) technology.
Machine Learning Approaches: ML algorithms are central to modern behavioral attribution. Hidden Markov Models (HMMs) infer unobserved states from observable events, crucial for understanding attacker progression. The clustering method in analysis groups unmarked data points according to their similarity characteristics which helps identify new behavioral groups or developing attack methods. The process of feature engineering converts unprocessed data into relevant ML model input features to enhance performance results.
Natural Language Processing (NLP): NLP evaluates linguistic characteristics in threat actor communications which produce unique linguistic profiles that show writing styles and vocabulary preferences.
Network Behavioral Analysis: The system examines DNS query patterns to find DNS tunneling and performs traffic flow analysis to detect both unusual data transmission and sustained server communication.
Practical Implementation Framework for Behavioral Attribution
A robust behavioral attribution system needs multiple architectural layers that combine advanced analytics with existing cybersecurity systems.
A Behavioral Attribution System requires four essential components to function: Data Collection Layer for precise logging capabilities and Feature Engineering Layer for data conversion and Analysis Engine for profile processing and score generation and Validation Framework for accuracy verification.
The core requirement for threat intelligence infrastructure integration involves seamless system connectivity. The system uses MITRE ATT&CK Integration for standardized context together with Threat Intelligence Feeds for dynamic behavioral profile updates and Standardized Sharing (STIX/TAXII) for secure behavioral indicator exchange.
Integrating Behavioral Biometrics with Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) operate as essential security tools that protect web applications and APIs by blocking malicious HTTP/S traffic. The integration of behavioral analysis and machine learning capabilities within modern WAF systems has made them essential tools for APT attribution purposes.
1. WAFs and Behavioral Analysis Capabilities Modern WAFs use behavioral analysis to surpass traditional static rules because they learn from application user and attacker behavior over time to detect abnormal traffic patterns and unusual behavior patterns. This is crucial for:
Real-time Anomalies: Detecting zero-day exploits or unknown attack vectors that lack predefined signatures.
Sophisticated Bots: Bots can be detected through analyzing real user interactions (e.g., pages visited, time spent, API call rates) when they mimic human actions or perform credential stuffing or execute “low-and-slow” Distributed Denial of Service (DDoS) attacks. Some WAFs can leverage client fingerprints by analyzing browser attributes, screen dimensions, cookie settings, and hardware-related details to differentiate real browsers from automated environments.
User Behavior Profiling: Establishing baselines of normal user behavior to flag deviations like impossible travel or rapid navigation through sensitive account areas, indicating automated scripts or malicious intent.
API Security: Baseling API behaviour, validating authentication, and visualizing API usage to detect anomalies and exposed sensitive data.
2. Data Collection and Integration WAFs generate detailed logs (timestamps, client IPs, URLs, user agents) that are foundational for behavioural analysis and can be integrated into broader security ecosystems:
Log Aggregation (SIEM): WAFs send logs, events, and alerts to a centralized Security Information and Event Management (SIEM) system for real-time correlation with other security events, providing a comprehensive security view.
Threat Intelligence Feeds: WAFs integrate with external threat intelligence feeds for up-to-date information on known malicious IPs and attack patterns, enhancing detection and prioritizing alerts.
SOAR Integration: Integration with Security Orchestration, Automation, and Response (SOAR) platforms enables automated responses to WAF-detected threats, such as quarantining devices or blocking IPs, streamlining security operations.
3. Policy Enforcement and Management Behavioural insights derived from WAFs dynamically update policies and enforce granular access controls::
Dynamic Policy Updates: Advanced WAFs leverage machine learning to automatically analyze security triggers for true attacks and false positives, developing policy-specific tuning recommendations.
Behavior-Based Rules: WAF policies prioritize behaviour-based anomaly detection, preventing requests with suspicious characters or imposing strict access restrictions based on behavioural baselines.
Zero Trust Integration: WAFs are essential enforcement points in a Zero Trust Architecture (ZTA), extending the principle of least privilege to the application layer by blocking unauthorized users, bots, and anomalous behaviours.
4. Benefits for APT Attribution By integrating WAF services with behavioural biometrics, organizations gain several advantages for APT attribution::
Early Detection of APT Activity: WAFs detect initial reconnaissance or infiltration attempts by APT groups targeting web applications, even if they use novel techniques, by identifying anomalous traffic patterns or unusual user behaviour.
Contextual Enrichment: WAF logs, when correlated with other security telemetry in a SIEM, provide rich context about web-based interactions, contributing to a more complete behavioural profile of an adversary.
Automated Response and Containment: SOAR integration allows for rapid, automated responses to WAF-detected behavioural anomalies, helping to contain potential APT activity before it escalates.
Reduced False Positives: By understanding contextual user behaviour, WAFs with behavioural analysis features can reduce false positives, ensuring that security teams focus on genuine threats rather than benign activities.
Real-World Case Studies: Demonstrating Behavioral Attribution Efficacy
Behavioral biometrics has proven instrumental in uncovering crucial clues in significant cyberattacks. WAFs, with their behavioural analysis capabilities, would play a crucial role in detecting the web-based aspects of these attacks.
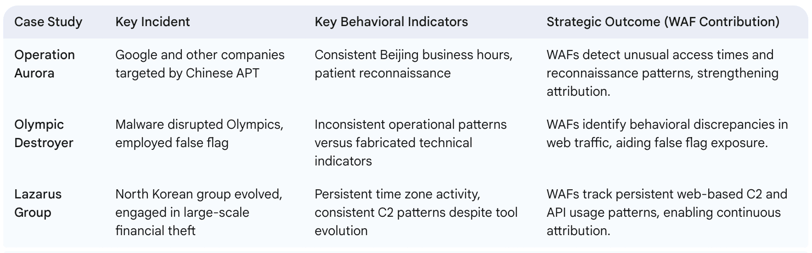
Case Study 1: Operation Aurora Attribution Enhancement: Operation Aurora Attribution Enhancement: The 2009 Operation Aurora attacks consistently occurred during Beijing business hours (UTC+8). A WAF, by analysing temporal patterns of web requests, could have flagged these unusual access times and reconnaissance patterns, strengthening attribution.
Case Study 2: False Flag Detection in Olympic Destroyer: The Olympic Destroyer malware famously included false flags to misdirect attribution. A WAF with behavioural analysis could have detected inconsistencies in web traffic patterns generated by the malware’s C2 communications or any web-based components, helping to expose the deception.
Case Study 3: Lazarus Group Evolution Tracking: The Lazarus Group has undergone substantial transformation throughout its evolution yet researchers have maintained tracking of the group through its consistent time-based patterns which match North Korean time zones and its standardized C2 beacon intervals. WAFs would prove essential for detecting these persistent web-based C2 and API usage patterns.
Challenges, Limitations, and Future Directions in Digital Fingerprinting
Digital Fingerprinting faces multiple obstacles in addition to its current challenges as an approach to APT attribution and WAF integration.
Challenges: The success of behavioral biometrics for APT attribution depends on two main factors: high-quality complete data and WAF integration to enhance accuracy. Behavioral drift necessitates WAF policies to adopt dynamic adaptation methods. The distinction between individual and collective APT behavior remains challenging to detect. The practice of digital fingerprinting raises important ethical and legal questions about privacy rights. APT actors attempt to blend their behavior with automated systems that reduce human fingerprints in their attacks.
Validation and Accuracy: The validation process requires rigorous testing through K-Fold Cross-Validation and false flag resistance tests. The evaluation of behavioral biometric systems depends heavily on their precision and recall metrics.
Best Practices: WAF logs must be included in comprehensive logging practices and data quality assurance must be robust to achieve success. Continuous learning through analyst feedback loops and model updating and integration with SIEM/SOAR remain fundamental for successful WAF deployment.
Future Directions: Quantum-resistant behavioral analysis and AI-powered behavioral synthesis (synthetic data) for training WAFs represent emerging technologies which will provide new capabilities in the future. The privacy-preserving model training method for WAFs known as federated learning allows organizations to collaborate without compromising security. The combination of advanced analytical methods including multi-modal analysis and causal inference with Explainable AI (XAI) will enhance attribution capabilities by building trust in WAF-driven decisions.
Conclusion: The Human Element as the Enduring Attribution Key
Behavioral biometrics has revolutionized APT attribution by moving organizations away from technical indicators which adversaries can easily manipulate towards human activities that sustain cyber operations. Organizations can build strong attribution capabilities through systematic analysis of temporal patterns combined with operational methodologies and technical preferences to achieve robust false flag resistance and actionable intelligence.
These systems need successful implementation with Web Application Firewalls (WAFs) requiring both precise data quality management and strict validation methods and ongoing learning practices. WAFs perform essential enforcement duties by analyzing complex web traffic behaviors which enables them to detect unusual patterns for attribution analysis. Organizations that invest strategically in these capabilities will develop a significant advantage in understanding adversary intentions while improving their ability to forecast attack methods and enhance defensive measures.
The future of cybersecurity will depend on behavioral biometrics integrated with WAFs as threat actors continue developing their operational security and deception techniques. The persistent human elements across various campaign tools and infrastructure evolution make behavioral biometrics the future of cybersecurity intelligence which enables professionals to develop more resilient attribution capabilities.
