Take Control, Let's Talk Cyber Defense!
WAF for Microservices and Serverless: Mastering Accuracy in Modern Architectures
Web Application Firewalls (WAFs) serve as essential security tools for modern architectures especially when used in microservices and serverless environments. WAFs now provide advanced security features including API protection and intrusion detection and bot management capabilities which make them indispensable for modern digital operations. The accuracy of WAFs requires proper management because improper configurations produce elevated false positive and negative results which harm business operations and user experience. Advanced WAF strategies combine rule optimization with AI-based anomaly detection and continuous monitoring. Organizations need to implement these technologies within their DevOps framework to build a security system which adapts to evolving threats.
5/22/202525 min read


I. Introduction: The Evolving WAF Landscape
Web Application Firewalls (WAFs) stand as fundamental components of application security because they demonstrate exceptional adaptability in protecting digital assets. WAFs have survived predictions about their future obsolescence by adopting adjacent security capabilities that now include Intrusion Detection/Prevention Systems (IDS/IPS) together with sophisticated bot management and Distributed Denial-of-Service (DDoS) protection and SSL decryption and complete API security functions. Their ongoing evolution through capability integration demonstrates their ongoing value in the current and emerging threat environment.
The WAF operates as a reverse proxy at Layer 7 (Application Layer) of the OSI model to scrutinize every HTTP/S traffic stream before it reaches the backend application server. Through its position as an intermediary the WAF performs request filtering and blocking functions to protect applications from various cyber threats. The flexible policy capabilities of contemporary WAFs enable quick attacks and application requirement adaptations through straightforward rule modifications.
WAFs have evolved through security functionality integration to become strategic network edge security orchestrators that go beyond simple signature-based blocking systems. Advanced tuning becomes essential because any misconfiguration affects numerous security controls that could result in extensive disruptions or significant security vulnerabilities.
The primary requirement for WAF deployment involves achieving maximum effectiveness in minimizing false positive and false negative occurrences. The achievement of this balance remains vital to preserve both strong security measures and operational efficiency and user experience quality.
False Positives: A WAF generates false positives when it incorrectly identifies regular user actions or harmless traffic as threats thus causing unnecessary blocking or complications. The negative effects of such errors have wide-ranging consequences across all operational areas:
Business Disruptions and Revenue Loss: your business suffers disruptions when legitimate transactions such as e-commerce sales and platform API communications become blocked. The financial impact leads to revenue reduction alongside higher cart abandonment rates and prolonged service interruptions
Poor User Experience and Customer Frustration: The experience of users deteriorates when they encounter login problems and excessive CAPTCHA requirements and API blockages which decreases customer trust and produces negative feedback.
Increased Security Team Workload: High rates of false positives create a significant workload burden for security teams because of alert fatigue. Security teams need to spend significant time on unneeded alerts which takes away from real threats and makes them miss important alerts.
Operational Inefficiencies: Internal applications together with APIs and workflows become unintentionally blocked which reduces employee productivity while generating additional IT support needs.
WAF tools exist in active "block mode" at a concerning rate of only 47% because organizations want to avoid false positives and misconfigurations according to research studies. These security measures lose their effectiveness because they function mainly as log analysis tools instead of active protection systems thus failing to stop important attacks like SQL injections and bot-based threats.
False positives in WAF systems stem from virtual patches that are too general and from suboptimal rule optimization and code snippets within submissions including HTML and JavaScript and SQL content and URLs matching attack signature patterns and special characters in form fields. The WAF produces unexpected responses to application updates which results in additional false positive events.
False positives from WAF systems create extensive effects on business operations and user experience as well as security team operational efficiency which demonstrates vital economic and reputational consequences. Organizations frequently prioritize avoiding the long-term costs of security breaches over the short-term costs of WAF tuning which creates a major business risk.
The technical challenge of WAF deployment transforms into a strategic business risk because organizations view the cost of WAF tuning as higher than the immediate danger of security threats. The widespread practice of not activating blocking mode in WAF systems demonstrates a fundamental trust problem in their security capabilities. Organizations hesitate to deploy WAF systems because they doubt the ability of these tools to execute their security functions without causing major adverse effects.
The solution demands both rule optimization and establishing trust through systematic evaluation and open monitoring and team-based improvements between security professionals and business stakeholders and application owners.
False Negatives: Conversely, the WAF produces a false negative result by missing actual security threats which allows harmful traffic to slip past defenses. The WAF's functionality suffers direct damage because of this which creates security team distrust and results in the most severe consequence of data exfiltration and potential breaches. Achieving proper security sensitivity and accuracy levels protects against both types of errors.
II. WAF Tuning Challenges in Modern Application Architectures
The deployment and optimization of WAFs faces new difficulties due to the distributed and transient and event-driven features of modern application architectures especially microservices and serverless platforms. The characteristics of distributed and ephemeral operations along with event-driven processing require organizations to reassess their Web Application Firewall deployment and optimization strategies.
A. Microservices Architectures
The fundamental structure of microservices involves separate deployable services which expose numerous API endpoints. The distributed structure of modern systems creates an enlarged attack surface.
Distributed Attack Surface and API Gateway as the Perimeter: Organizations widely use secure API Gateways to establish a first line of defense through the distributed attack surface. The gateways function as single access points to handle all traffic while performing routing and authentication as well as authorization functions and request modification. The API Gateway functions as the main defensive position for Web Application Firewall protection because it stops widespread attacks before they reach individual microservices. The placement of WAFs at the perimeter is essential for protecting external client requests entering through the gateway.
The security community advises organizations to use API Gateways as the single entry point and place WAFs in front of every API because these gateways serve as the primary strategic WAF enforcement point in microservices environments. The centralization of external traffic protection through this position makes it simpler to establish WAF protection for north-south traffic at the beginning.
The WAF operating at this level must demonstrate advanced capabilities to handle multiple API endpoints while avoiding false positives for authorized API consumers. It also needs comprehensive knowledge about API standards and authentication protocols together with versioning capabilities to execute proper traffic inspection.
Securing East-West Traffic: The Service Mesh Imperative: The Service Mesh Imperative: Traditional WAFs demonstrate insufficient capability to detect east-west traffic threats while API Gateways succeed in protecting north-south traffic which connects clients to services. Threats which begin from internal network traffic can result in major system breakdowns and enable attackers to move between internal systems.
The implementation of Service Mesh represents an essential requirement. The service mesh infrastructure which includes Istio exists to manage security and control the communication flows between microservices networks. This security solution delivers fundamental capabilities which include service discovery and load balancing and circuit breaking alongside robust security features for inter-service data exchange.
The security enhancement through service meshes depends on mutual TLS (mTLS) between service nodes to verify identity before data exchange occurs. The system perimeter becomes less dependent because the solution fights man-in-the-middle attacks. WAF solutions from modern times are developing to bridge this security gap.
The deployment technology of SafeLine operates within Service Meshes through embedded T1K modules in sidecars to protect east-west traffic by implementing API security measures with user behavior detection and permission anomaly monitoring and malicious traffic protection capabilities.
Traditional WAFs struggle with east-west traffic security which is why service meshes work as a complementary security solution for inter-service communication networks. The WAF tuning requirements for microservices surpass perimeter protection to include API interaction security which needs rules that identify service communication patterns instead of web request patterns.
The security transition from network-based protection to application-based defense requires WAFs to function either as sidecars or merge seamlessly with service mesh policies. The requirement for API security and permission anomaly monitoring of east-west traffic along with mTLS understanding and service node entry points establishes that least privilege access principles must apply to both human users and service communications. Service mesh integration with WAFs allows organizations to establish precise policies which restrict compromised services from performing malicious interactions with other services. WAF rules need to understand service identities and authorized communication patterns to enforce security policies beyond basic attack signatures because they require service-to-service contract knowledge.
API-Specific Rule Management Complexity in Microservices: The microservices architecture introduces major complexities for communication management because it involves tens to hundreds of standalone services.Each service operates with specific APIs which offer unique functionality together with different data structures and defined response patterns.
The API gateway performs smart traffic routing using path-based and header-based and API version-based rules. Routing flexibility in WAF requires rules that are both granular and context-aware. Generic WAF rules generate high rates of false positive and false negative results when used to protect various APIs.The numerous microservices and requirement for "API-specific WAF rules" create a challenge between achieving detailed security protection and keeping WAF policies under practical control. Maintaining specific security rules for hundreds of APIs through manual development proves both unsustainable and prone to errors.
WAF management needs to transform into a software engineering problem because of the strong requirement for automation and policy-as-code and potential AI/ML-driven rule generation or adaptation systems to handle the dynamic nature and scale of microservices.
B. Serverless Architectures
Traditional WAFs cannot protect serverless workloads effectively because each function instance remains stateless and short-lived and discards all state information after a single use.The serverless function scalability and cost efficiency depend on this fundamental characteristic but introduce specific security challenges to traditional WAF systems that need session persistence.
Ephemeral and Stateless Nature: Behavioral analysis systems within WAFs track user and attacker interactions throughout time to identify abnormal patterns which deviate from previously established baselines. The nature of serverless functions makes it difficult to create enduring behavioral patterns for function instances because their servers permanently change between executions.
Modern WAFs conduct behavioral analysis through edge-based request pattern inspection but need to implement their own session context system or connect to external state management tools (e.g., distributed caches, managed session stores) to create user profiles across multiple brief function calls. The core challenge of statelessness for WAF behavioral analysis indicates the WAF cannot store session state within ephemeral function instances.
The WAF located at the edge needs to become stateful or integrate with external state management systems to create behavioral analysis user profiles. The responsibility for session persistence now falls on the WAF layer together with its supporting infrastructure so WAF providers need to develop complex user behavior tracking systems for stateless interactions.
Event-Driven Paradigms - Protecting Invocation Points: The core nature of serverless applications depends on event-driven operations because functions start their execution through various triggering elements. Lambda functions receive their triggers from HTTP requests through API Gateway yet serverless functions can start from different event types including S3 bucket changes and SQS queue messages and DynamoDB table updates.
WAFs act as edge layer security tools to inspect potential threats that would otherwise reach serverless workloads through their main HTTP/S API Gateway endpoints. The security solutions available for inspecting HTTP/S traffic form the basis of traditional WAFs. Internal event sources that activate Lambda functions such as S3, SQS, and DynamoDB Streams bypass the traditional HTTP-aware WAF completely. This creates a significant "invisible" attack surface.
The combination of non-HTTP event triggers for serverless functions generates a substantial attack surface which traditional edge WAFs fail to defend. Security measures for serverless require attention to both event source protection and internal function validation logic instead of depending on WAF perimeter security. Security in serverless operations demands a shift-left strategy which moves security validation closer to both function code and trigger points. The event sources that activate serverless functions alongside WAF limitations to HTTP protocols require more than one security point at the API Gateway.
Security controls must develop awareness about event sources because they require this capability. These security controls require understanding of the structural elements and typical data patterns in S3, SQS and DynamoDB Streams to detect malicious data injections or abnormal behaviors before Lambda function execution or during Lambda function processing. This security requirement transcends WAF capabilities into cloud-native application protection platforms (CNAPPs) and serverless security tools that can analyze and filter data in non-HTTP events.
Cost-Exhaustion (Denial-of-Wallet) Risks: Serverless computing models with auto-scaling and pay-as-you-go payment systems enable cost efficiency but create a crucial security vulnerability known as Denial-of-Wallet (DoW) attacks. The trigger of an uncontrolled high number of function calls through malicious activity or programming mistakes results in rapid resource utilization followed by unexpected high cloud expenses.
Rate limiting stands as an essential security measure for fighting both Denial-of-Wallet (DoW) and Distributed Denial of Service (DDoS) attacks by setting boundaries on serverless function request quantities. Organizations must set rate limits correctly since improper settings can cause resource exhaustion and result in uncontrolled financial expenses. The direct financial implications of excessive function invocations transform WAF rate limiting functions from basic security tools to essential financial governance mechanisms.
The main objective of WAF tuning for serverless environments extends past blocking attacks since it must also prevent sudden unexpected cloud expenses. WAF rules must receive precise cost-conscious tuning because of this requirement. A combination of financial and security views requires cost monitoring tools with alarm functions to enable total visibility. Both security and financial posture.
III. Advanced Strategies for Minimizing False Positives and Negatives
The deployment of WAF tuning in contemporary application systems demands a mixture of essential enhancements and advanced technologies along with security operations integration within development workflows.
A. Foundational Tuning Refinements
Continuous Testing and Iterative Rule Lifecycle: The process of managing WAF rules needs to be continuous and iterative to achieve advanced WAF tuning. Testing WAF rules in a regular manner remains essential for obtaining both accurate and precise results which minimizes errors in both false positives and false negatives.The WAF operates in "Log Mode" (also known as "Count Mode") when deploying new or modified WAF rules to the network.
The WAF system logs suspicious traffic that matches the rule while avoiding actual blockages during this mode. Security teams benefit from this approach because they can evaluate rule effectiveness before fixing false positives while preserving legitimate application traffic flow. The transition from "Log Mode" to "Block Mode" should occur after a thorough testing period of several days or one week.
A "security-as-code" methodology requires organizations to maintain WAF rules inside their application codebase. Storing WAF configurations along with rules in version control systems (like Git) enables complete change tracking and seamless rollbacks as well as collaborative security tuning in DevSecOps pipelines. The "continuous testing" and "frequent updates" approach combined with the "Log Mode before Block Mode" process matches the fundamental principles of modern software development continuous delivery methods.
WAF tuning operates as an active procedure that repeats itself throughout time instead of requiring one-time setup. By including WAF rule management in CI/CD pipelines organizations convert security into a continuous feedback system which remains crucial for maintaining high agility and accuracy across dynamic cloud environments. Such approach helps operations teams and development teams share security responsibilities together.
Application Profiling and Intelligent Whitelisting: Using WAF intelligence to generate profiles of normal application activity enables organizations to transcend basic negative security methods which focus on blacklisting known malicious patterns. The WAF should be used to generate profiles from normal application behavior instead of traditional negative security models (blacklisting known bad patterns).
Create detailed documentation of both typical traffic behavior and acceptable input data and approved API operations. Profiling data allows organizations to create whitelisting (positive security models) which allows only approved traffic patterns and rejects all other communications.
Some modern WAF solutions contain built-in profiling and whitelisting functionality which reduces the complexity of implementing these features. The defined 'normal' baseline allows the system to detect zero-day or unknown threats while minimizing false positives for legitimate traffic. The suggested method of "profiling + whitelisting" with "positive security model" represents a stronger security approach yet presents greater complexity than blacklisting.
Current modern systems experience growing difficulty in identifying every malicious element. By establishing profiles of known good traffic the system reduces false positives for legitimate traffic while improving its ability to detect unknown threats by marking deviations from the established baseline. The implementation of this method demands both strong application logic comprehension along with a WAF system that possesses behavioral learning capabilities.
Granular Rate Limiting and Sophisticated Bot Management:
Rate Limiting: Rate Limiting should be implemented to restrict the volume of requests to web applications and APIs with granular rate limiting. This is important to prevent overload, to mitigate Distributed Denial-of-Service (DDoS) attacks and to control the potential cost-exhaustion (Denial-of-Wallet) risks in serverless environments. Advanced WAFs provide adaptive rate limiting, which adjusts thresholds based on real-time traffic patterns to improve accuracy and prevent blocking of legitimate users during traffic spikes.
Bot Management: Implement sophisticated bot management capabilities to distinguish between human users and “good” bots (e.g., search engine crawlers) and “bad” bots (e.g., scrapers, credential stuffers, automated attack tools).Advanced WAFs use a combination of static detection (analyzing HTTP requests), behavioral analysis (flagging scripted or automated access patterns), and bot scoring to allow good bots while blocking or rate-limiting malicious ones. The evolution from basic “rate limiting” to “adaptive rate limiting” and sophisticated “bot management” indicates a move beyond simple throttling. It is about intelligent traffic shaping that understands the intent behind the requests. This is very important in modern applications where legitimate automated traffic (APIs, integrations) coexists with malicious bots, requiring WAFs to make intelligent decisions to avoid blocking legitimate business processes while effectively mitigating threats. This requires WAFs to use advanced analytics and machine learning to distinguish between human and automated traffic.
OWASP Top 10 and API Security Alignment: WAF rules and policies should be specifically designed and continuously tested to mitigate vulnerabilities listed in the OWASP Top 10, which represents the most critical web application security risks.Given the API-centric nature of microservices and serverless, WAF tuning must be aligned with API security best practices. API Gateways, where WAFs are often deployed, centralize authentication (e.g., OAuth2, JWT) and enforce security policies to block malicious API traffic.
WAF rules should be tailored to the specific API endpoints, understanding their expected inputs, outputs, and authentication mechanisms. WAFs are not just generic web protectors but specialized API security enforcers. The explicit mention of OWASP Top 10 and API security indicates that WAFs are not just static web protectors but dynamic API security enforcers.
Since microservices heavily rely on APIs, WAF tuning must align with API design principles, understanding API schemas, expected parameters, and authentication mechanisms to effectively protect against API-specific threats like broken authentication or excessive data exposure. This requires a WAF that can understand complex API payloads and apply specific rules based on API endpoints and methods.
B. Leveraging AI/ML and Behavioral Analytics
Real-time Anomaly Detection and User Behavior Profiling: Real-time Anomaly Detection and User Behavior Profiling: The modern WAFs use Artificial Intelligence (AI) and Machine Learning (ML) for real-time detection beyond the traditional signature-based detection methods. Behavioral analysis examines how users and attackers interact with an application over time to identify abnormal patterns, discrepancies, and deviations from established baselines.
This includes tracking user journeys, pages visited, time spent, and typical API call rates to identify anomalies in real-time.AI-powered threat detection and behavioral analytics are specifically effective for improving serverless threat detection.The advantages are many: zero-day or unknown attack vector anomaly detection in real-time, significant reduction in false positives by understanding contextual user behavior, enhanced bot mitigation through advanced pattern recognition, and improved visibility into user journeys and potential abuse patterns.
The shift from “static rules” to “behavioral analysis” and “AI-powered anomaly detection” represents a fundamental paradigm shift. Traditional WAFs are reactive, relying on known signatures. AI/ML-driven WAFs are proactive, learning “normal” and identifying “abnormal,” which is important for detecting zero-day threats and sophisticated evasion tactics that mimic legitimate traffic.This means that WAFs should be able to process and consume a lot of traffic data to build accurate baselines in order to be intelligent and less dependent on manual rule updates.
Adaptive Learning for Dynamic Rule Optimization: AI/ML-operated WAF solutions implement adaptive learning capabilities that modify security rules in real time. This allows them to detect zero-day vulnerabilities and prevent automated bot attacks by not depending on predefined rule sets or manual updates.Adaptive learning engines conduct deep packet inspection and traffic analysis to construct comprehensive datasets from traffic patterns. Using these insights, they can autonomously identify threats, generate tailored recommendations to refine protection policies, and even automatically apply basic WAF policies for new application profiles.
For example, Google Cloud Armor’s Adaptive Protection constructs ML models to detect abnormal activities, create a signature that defines the potential attack and then produce a custom WAF rule to stop that signature.This iterative process includes identifying false positive triggers to adjust policy settings.The concept of “adaptive learning” and “automated WAF rule optimization” suggests a future where WAFs are more self-optimizing. This directly addresses the manual and time consuming process of tuning and the need to keep up with evolving threats.
For complex, dynamic environments like microservices and serverless, this automation is not just a convenience but a necessity to keep the accuracy and effectiveness at scale, allowing security teams to focus on high-level strategic concerns.
Integrating Threat Intelligence Feeds: WAFs at their most advanced stage combine threat intelligence feeds that receive input from both internal security teams and third-party providers in real-time. Threat intelligence feeds deliver current information about known malicious IP addresses as well as malicious URLs and domains and cybercriminal operational methods (TTPs).
The WAF can effectively block evolving threats through its real-time threat intelligence feed integration. The WAF uses new security measures to combat particular threats when it detects new vulnerabilities or active botnets. Through its dynamic approach the WAF improves its ability to differentiate between regular and dangerous network traffic. WAFs function beyond their traditional role as standalone security devices because they operate as connected nodes that enhance broader security systems through threat intelligence integration. WAFs defend against known and emerging threats more effectively through collective intelligence integration that minimizes the need for individual rule creation.
The value of WAF systems depends more and more on their capability to receive and transform external threat information into a security enforcement platform for global threat detection.
C. Operationalizing WAF in CI/CD/DevSecOps
Automated WAF Configuration and Policy-as-Code: Manual security setups can slow down modern DevSecOps processes and increase the chances of mistakes. Automating the setup and deployment of Web Application Firewall (WAF) is really important for keeping security consistent in all stages of development, while also lowering the chance of errors and compliance issues. "Policy-as-Code" (PAC) helps with this automation by allowing WAF rules and policies to be written in easy-to-read formats like YAML or JSON, making it easier to manage them automatically. This way, security settings can change quickly to respond to new threats or updates without needing to do it all by hand.
By treating WAF rules like part of the application code stored in Git, it becomes easier to track changes, roll back if something goes wrong, and work together on improving security. This shift towards automation and managing WAF rules in Git means that WAFs are no longer an afterthought but are now a vital part of creating software. It allows developers to set and test WAF policies while they write code, making everything faster and reducing mistakes, while promoting a culture where everyone shares responsibility for security in the whole development process.
Centralized Log Analysis and SIEM Integration for Enhanced Observability: Seeing what's happening with the Web Application Firewall (WAF) in real time is really important for spotting and handling security issues quickly. You should connect WAF logs to your current security tools (like Splunk, ELK Stack, AWS Security Hub, or Microsoft Sentinel). This way, security teams can link alerts from the WAF with other security data in the organization, helping them understand the overall security situation better and making it easier to spot threats and respond to them.
Using automatic log analysis can help find patterns in attacks, reduce false alarms, and fix any operational problems, making sure WAF rules stay effective and get better over time. Cloud-based security tools can use AI to improve how they detect and respond to threats. For example, AWS WAF logs can be saved in Amazon S3 or CloudWatch Logs and analyzed by special Lambda functions for more advanced insights and automatic blocking of threats.
The focus on connecting WAF logs with security tools and using automated analysis shows that monitoring isn't just for fixing problems, but also for constantly improving WAF performance and accuracy. Without clear and useful logs that can be analyzed easily, finding false positives or negatives and changing rules becomes a complicated and error-prone job. This makes WAF logs really important for learning and building trust in how well the WAF works.
Virtual Patching for Agile Vulnerability Response: WAFs, or Web Application Firewalls, have a cool feature called "virtual patching." This lets companies protect their apps from security issues without having to change the app's code or completely restart it right away. When a security team spots a new problem (like a zero-day exploit), they can set up a custom rule in the WAF to block any attacks trying to take advantage of that issue. This gives developers extra time—sometimes weeks—to fix the app properly, making updates easier and less disruptive. Virtual patching is super important because it helps balance the need for quick updates with the need for strong security. It means security teams can manage new risks without rushing to change the code, which can be a slow and tricky process. This way, businesses can avoid major disruptions from sudden threats and stay flexible in their security efforts, making it easier to handle long-term fixes later on.
IV. Practical Implementation and Case Studies
Practical WAF tuning and optimization in modern application architectures involves specific deployment patterns and considerations for both microservices and serverless environments.
A. Microservices Deployment Patterns
WAF with API Gateways: In microservices, API Gateways are like the main doors for all requests from users. They are perfect places to add Web Application Firewall (WAF) security. Cloud companies, like AWS, provide WAF services that work directly with their API Gateway and Load Balancer tools. For example, AWS WAF easily connects to services like Amazon API Gateway and Application Load Balancers (ALB). This means you can link a web Access Control List (ACL) to an API Gateway stage or an ALB. Even if you're using a Network Load Balancer (NLB) to get a static IP address, you can still use an ALB as a target and protect it with AWS WAF. A key point is that the NLB keeps the original IP address of traffic sent to the ALB, which helps WAF rules work correctly. Keeping the client IP is important for things like limiting requests, spotting bots, and checking if an IP is trustworthy. If the client IP isn’t preserved or is sent incorrectly, like in certain headers (e.g., X-Forwarded-For) that some AWS rules don’t support, the WAF can’t make good decisions. This leads to wrongly identifying threats or missing actual ones. This shows that choices made before the WAF affects how well it works and how precise it is.
WAF Integration with Service Meshes: To keep east-west traffic safe in a microservices setup, using a Web Application Firewall (WAF) together with a service mesh is a cool new method. OWASP Coraza is an open-source WAF that uses a set of rules called the ModSecurity Core Rule Set (CRS). It is fast and can handle lots of traffic, making it perfect for modern microservices. Coraza can work as a sidecar proxy in an Istio service mesh, which helps in managing and growing WAF features in a Kubernetes environment. This setup helps check and protect the communication between different services. Coraza also lets you easily change the CRS rules, including making exceptions, adjustments, and adding your own rules with ModSecurity syntax, giving you detailed control over the security of internal traffic.
Case Study Example (OWASP Coraza with Istio):
Online Retailer: A big online store used Coraza WAF with their Istio service mesh to keep their shopping website safe. By taking advantage of Coraza's smart rules and performance improvements, they managed to block a lot of SQL injection and cross-site scripting attacks while still making sure that users had a smooth experience on their site.
Financial Institution: A worldwide bank used Coraza WAF to keep their online banking and trading websites safe. By connecting it with their other security tools and keeping an eye on potential threats, they could spot and deal with new dangers early, which helped lessen financial losses and protect their reputation.
Government Agency: A government agency that handles important citizen information used Coraza WAF to keep their websites safe from unauthorized access and data theft. They used detailed access controls and rules to prevent data leaks and ensure that the information stayed private and secure.
OWASP Coraza's success shows that open-source, community-supported web application firewalls (WAFs) can work really well, especially when paired with other cloud tools like Istio. This means that companies don’t always have to buy expensive WAFs; they can create strong security systems using flexible and customizable open-source tools made for today’s tech. However, this also means companies will need skilled people on their team to manage and improve these tools, shifting their spending from paying for licenses to investing in their own talent.
Table: Microservices WAF Tuning Considerations
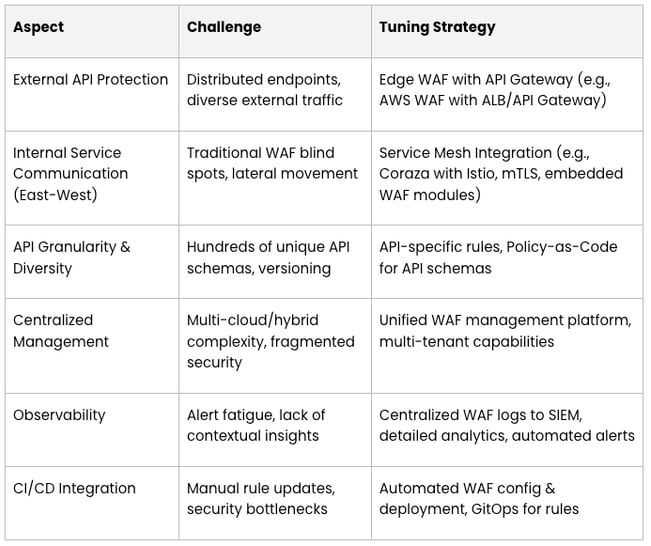
B. Serverless Deployment Patterns
Edge WAF for Lambda-backed APIs: For serverless applications that use HTTP/S, the main place to set up a Web Application Firewall (WAF) is at the edge, which is usually in front of API Gateways that activate Lambda functions. Cloud providers have built-in WAF solutions for these services. For example, AWS WAF can be linked to Amazon API Gateway REST APIs. It helps detect threats, analyze behavior, and filter bad IP addresses before requests reach the serverless tasks. Other solutions like F5 BIG-IP WAF can also be used to protect API Gateway, which can run serverless Lambda code, offering features like DDoS protection, managing bots, and checking authorization. The fact that WAFs are placed "at the edge" along with "API Gateways" for serverless systems highlights that the API Gateway is the main point for enforcing WAF rules. This means that when setting rules for serverless APIs, you should focus a lot on the WAF settings related to the API Gateway, including limiting how often requests can be made, protecting against bots, and detecting signatures. It also means the WAF needs to work closely with what the API Gateway can do, like using Lambda authorizers and managing usage plans.
Addressing Statelessness for Behavioral Analysis: The way serverless functions work makes it tricky for traditional security systems to track user activity like they usually do. Since these functions run for a very short time, the security system, often located at the edge of the network, still needs to analyze user behavior to spot unusual patterns. To do this, the security system must either keep some user session information or connect to permanent storage solutions (like databases) that collect user activity data over time. This helps the security system create a clear user profile, which is important for accurately detecting odd behavior and reducing false alarms. Because serverless functions don't have a built-in way to keep track of sessions, advanced security systems need to either manage their own user data storage or use cloud services (like Redis or DynamoDB) to gather this information. This setup is crucial for effective security in serverless environments, allowing systems to maintain user profiles that help them identify real threats without flooding users with false alerts.
Protecting Non-HTTP Event Sources: A key part of keeping serverless applications secure is that functions can be triggered by various sources that don't use traditional web traffic, like when a file is created in S3, a message is sent to SQS, or updates happen in DynamoDB. Regular web application firewalls (WAFs) only protect HTTP/S traffic, so they don’t guard these internal triggers, leaving them open to potential attacks if they're not secured properly. To keep these internal triggers safe, it’s important to have strong access controls to limit who can do what (using the Principle of Least Privilege), encrypt data, and carefully check all incoming data in the function code.
Even though WAFs don't protect these triggers directly, their logs can be used with cloud services like AWS EventBridge and Step Functions to automatically check for security issues. Since WAFs don’t cover these non-web triggers, securing serverless applications requires a broader strategy beyond just WAFs. This emphasizes the shared responsibility model, where the cloud provider takes care of the infrastructure, but users need to secure their code, settings, and event sources. Therefore, working on serverless security includes not only setting WAF rules but also managing permissions, validating inputs in functions, and monitoring non-HTTP event streams for any irregularities, making security a deeper part of the application logic.
Table: Serverless WAF Tuning Strategies
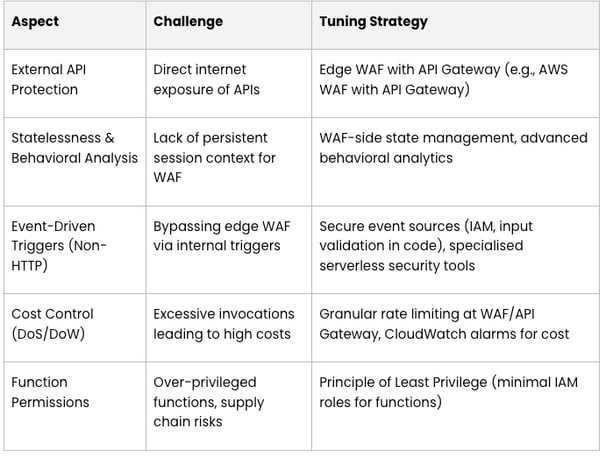
V. Common Pitfalls and Anti-Patterns to Avoid
Effective WAF tuning is as much about implementing best practices as it is about avoiding common pitfalls that can undermine security posture and operational efficiency.
Over-reliance on Default Rules and Signatures: A big mistake is thinking that the basic web application firewall (WAF) rules or rules from vendors are enough for complete protection. While these rules are a good start, they're usually pretty generic and might not work well with specific app features, traffic patterns, or unique APIs. Relying too much on them can lead to blocking real users (false positives) or missing out on clever attacks (false negatives). Regular WAFs, which follow set rules, are good against known attacks but fail against new or complicated threats that don't fit usual patterns. They also can't fully mimic how users interact with the app or catch problems that come from complex processes.
Neglecting East-West Traffic Security: Traditional web application firewalls (WAFs) usually protect the flow of data coming in and going out of a system ("north-south" traffic), but they don't really guard against the communication happening between different services inside that system ("east-west" traffic). In setups using microservices, this internal communication can be a big target for hackers looking to move around unnoticed and cause problems. If we don't add security measures, like connecting WAFs with service meshes or setting up detailed security for APIs inside that mesh, we're leaving a huge gap that attackers can take advantage of.
Lack of Continuous Monitoring and Feedback Loops: Using a Web Application Firewall (WAF) without keeping an eye on it is a bad idea. If it keeps giving false alarms, the security team might get tired of checking them and could miss real attacks. If no one is regularly checking the WAF's logs and improving its rules, it won't be able to handle new threats or changes in how the app works. This turns it into an old defense system that doesn’t work well anymore.
Misconfigurations and Their Business Impact: Security mistakes happen a lot, especially when settings are wrong or not set up fully, or when old, unsafe default settings are still in use. These issues can make important systems vulnerable to attacks, which can cause data leaks, money losses, fines from regulations, and problems in how things run. For Web Application Firewalls (WAFs), mistakes in setup can lead to:
Overly Permissive Rules: Allowing too much traffic, effectively nullifying the WAF's protection.
Overly Restrictive Rules: Causing excessive false positives and business disruption.
Improper Logging: Failing to capture necessary data for forensic analysis or rule tuning.
Neglecting Updates: Not applying security patches or updating WAF rules, leaving known vulnerabilities unaddressed.
Misconfigurations happen a lot because people make mistakes, don’t understand security well, or because modern cloud systems are really complicated. Studies show that many problems with cloud security come from user errors and misconfigurations. For example, the Capital One data breach in 2019 happened because someone took advantage of a misconfigured firewall, which let them access sensitive data stored in S3 buckets.
The "False Sense of Security" Trap: Depending only on a Web Application Firewall (WAF) can create a misleading feeling of safety, making organizations ignore other important security steps. Attackers are always coming up with clever ways to get around security measures, using tricks like encoding, pollution of HTTP parameters, and pretending to be normal traffic patterns to fool even advanced machine learning-based WAFs. WAFs mainly deal with web traffic but don’t fix problems in the application code itself. So, a WAF should just be one part of a complete security plan. This plan should also include writing secure code, regularly checking for vulnerabilities, testing for weaknesses, and strong application security testing during development. Without these extra steps, companies are still at risk of serious vulnerabilities.
VI. Conclusion: Building Resilient and Accurate WAF Defenses
Web application security is changing quickly because more people are using complicated systems like microservices and serverless setups. Although Web Application Firewalls are still a crucial first step in protecting websites, they work best when they are set up and fine-tuned to deal with the specific problems that come with these new technologies.
These are key principles we recommend for building resilient and accurate WAF defenses.
Focus on Getting it Right: The problem of wrong warnings means we need to carefully set things up. WAFs should first run in a "Log Mode" to check things before they start blocking anything, making sure real users can still access the site while stopping bad stuff from happening.
Understand the Setup: Basic WAF settings don't work for everything. For systems that use smaller services, it's important to place them at API Gateways for main traffic and connect them with service meshes to protect data moving between services. For serverless setups, edge WAFs safeguard functions but need to handle temporary sessions and look at security for non-HTTP events differently, bringing validation closer to what the function code does.
Use Smart Technology: Moving from basic detection methods to advanced AI-driven analysis is essential to find new and clever ways attackers might bypass security. Using real-time threat information makes the WAF better at preventing attacks.
Make Security Part of Development: Treating WAF settings like "Policy-as-Code" in development cycles (CI/CD) allows for automation and speed. Keeping logs in one place and using SIEM lets us continuously adjust and respond quickly to issues. Virtual patching helps give developers time to fix code issues properly.
Watch Out for Mistakes: Relying too much on default rules, ignoring internal traffic, not monitoring effectively, and setting things up wrong can lead to problems. A WAF is just one part of a larger security plan, not a catch-all solution.
In the future, Web Application Firewalls (WAFs) will get smarter and work more automatically as part of how apps are built and released. As apps become more spread out and change quickly, WAFs will adapt by using advanced data analysis to understand how apps behave, updating their rules on the fly, and providing protection across different events and service communications. This change will turn WAFs from just reacting to threats into proactive security systems that optimize themselves, which is important for staying accurate and strong against increasing cyber threats.
